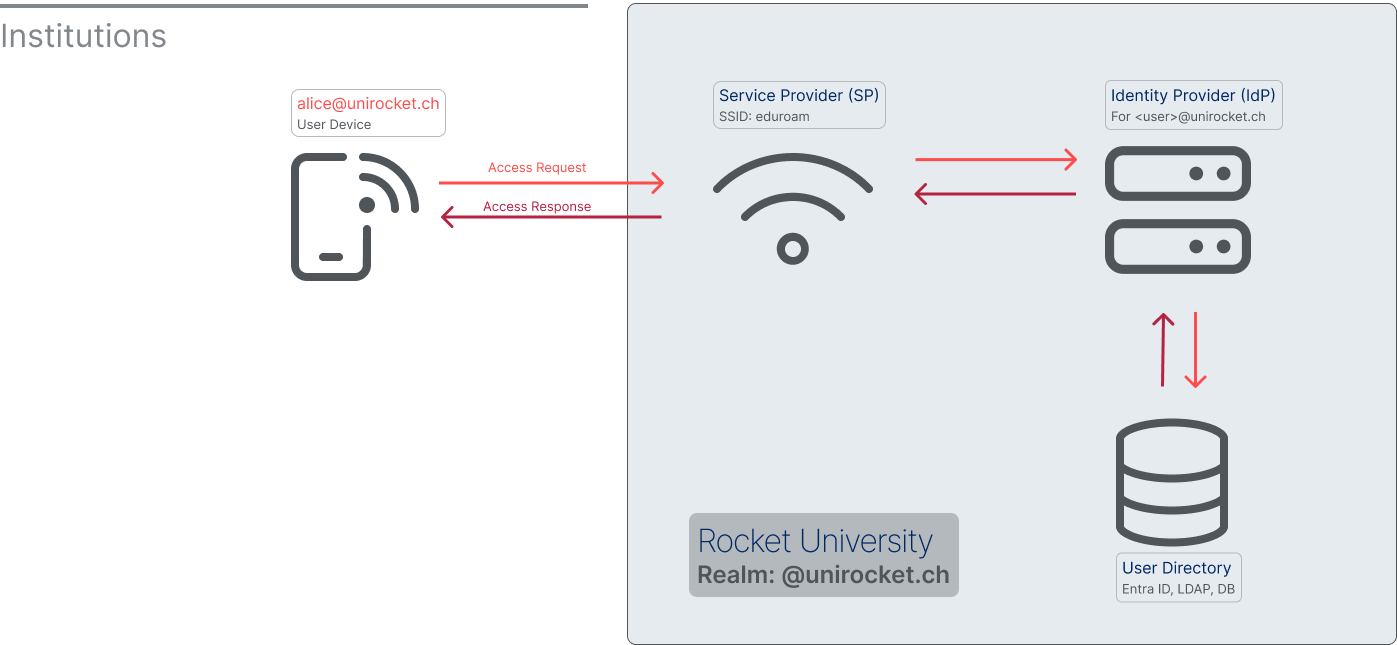
Identity Provider (IdP, Authentication Server)
Radius Server (FreeRADIUS, NSP, ISE)
|
|
eduroam with edu-ID | Classic IdP | Radius Hosting | Managed IdP |
| Description |
Do your users have an edu-ID? Give them access to eduroam using edu-ID or Entra ID |
Run your own RADIUS infrastructure connected to your user directory | Outsource configuration and operation of the RADIUS infrastructure to Switch | Create eduroam user accounts manually. Ideal for institutions with a small user base. |
| Strengths |
|
|
|
|
| Weaknesses |
|
|
|
|
'eduroam with edu-ID' IdP
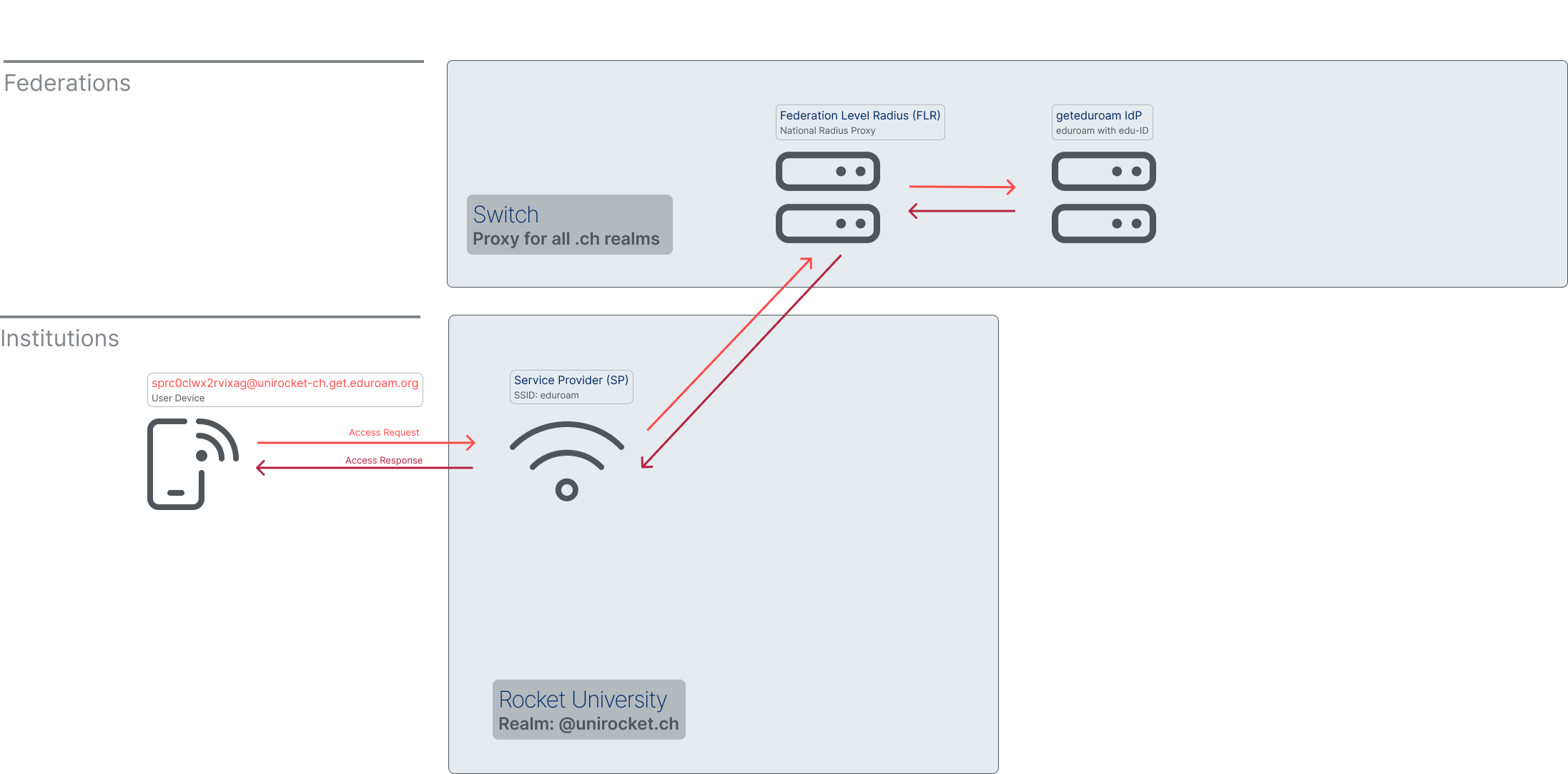
The eduroam consortium operates a RADIUS infrastructure - one of the nodes hosted on the Switch Cloud - which is registered as a service in the eduGAIN interfederation. User can use their edu-ID (or Entra ID) to download and install a secure certificate-based eduroam profile.
Organisations on the other hand can decommission their local RADIUS infrastructure and eliminate the risk that user misconfigure their eduroam access or even leak their credentials to untrusty counterparts.
This IdP can optionally provide information about the user in the realm based on the 'eduPersonAffiliation' attribute with typical values being student, staff, alum or affiliate. This can be leveraged for VLAN assignment at the institution.
Switch encourages institution to consider switching from their self-hosted RADIUS server to this approach. Experience from institution that have migrated show that the number of support cases decreases dramatically when using this method in conjunction with the geteduroam app.
Please get in contact with us if you would like to enable 'eduroam with edu-ID'. This IdP can run in parallel with an already existing classic IdP, so you can do initial tests with it while still maintaining your proven RADIUS infrastructure. You might also want to consider using this method for your students, while keeping the on-prem IdP for your staff.
Radius Hosting
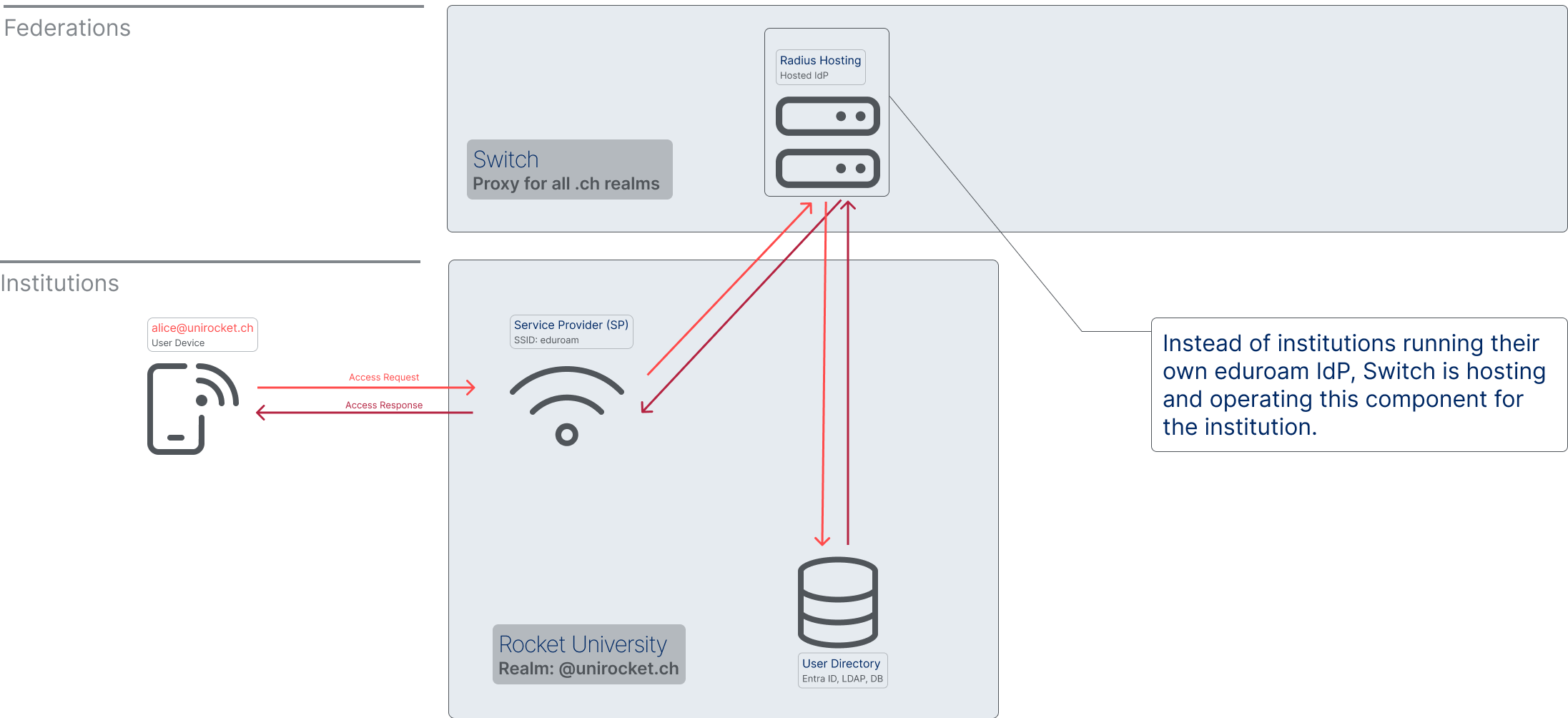
In this scenario, Switch is hosting and operating the IdP of the institution with the user authentication still happening against the user directory of the institution. With 'Radius Hosting' the institution doesn't need to run their own IdP anymore.
This service is fee-based. It is a good alternative for institutions that for some reason can't do 'eduroam with edu-ID/Entra ID', but don't want to operate their own IdP.
Managed IdP
The managed IdP is suitable for smaller institutions that don't want to operate their own RADIUS server and are not providing SWITCH edu-IDs to their users.
User are being manually managed by the administrators of the organisation in the web interface. There is an additional option to create multiple user at once via batch upload, but we currently enforce a limit of 100 users per institution. Use of this service is subject to a charge.
Once the users are successfully created, they can be invited to download an eduroam profile for installation on their devices.