Expert Session Add-On
This additional explanation covers the sessions at the Identity Provider and
the Service Provider.
It illustrates the different flows in case the user has already a valid session at the one of them.
Furthermore, some facts about Shibboleth sessions are outlined and it is shown what data is contained in a valid session and which information is bound to a
session.
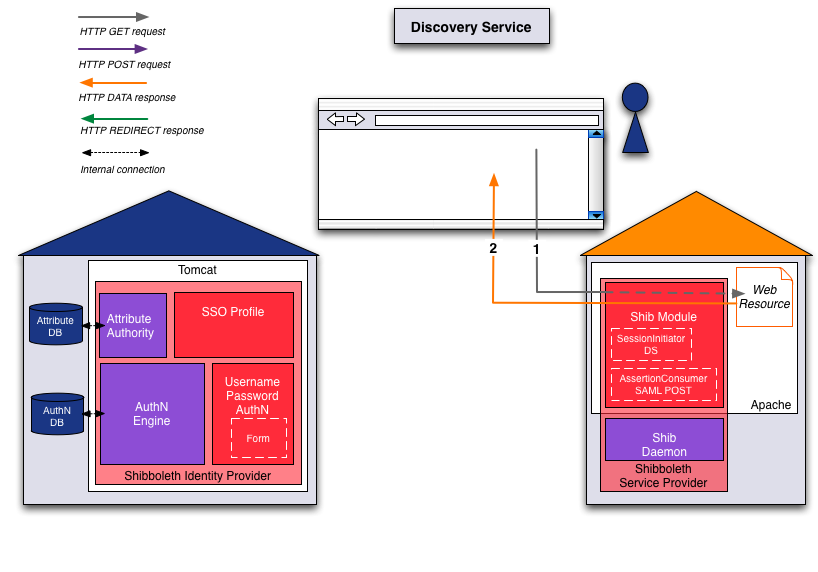
SP Session
The Service Provider checks:
- If a session already exists for the user
- If the session timeout (user inactivity) is not exceeded (default: 1h)
- If the session lifetime (maintainance in cache) is not exceeded (default: 8h)
- If the maximum time since the last authentication is not exceeded (default: not set)
Data bound to a Service Provider session is:
- Attributes
- Authentication information (time, method, class, ...)
- ...
This means that all authorization and access checks are done from the session bounded data.
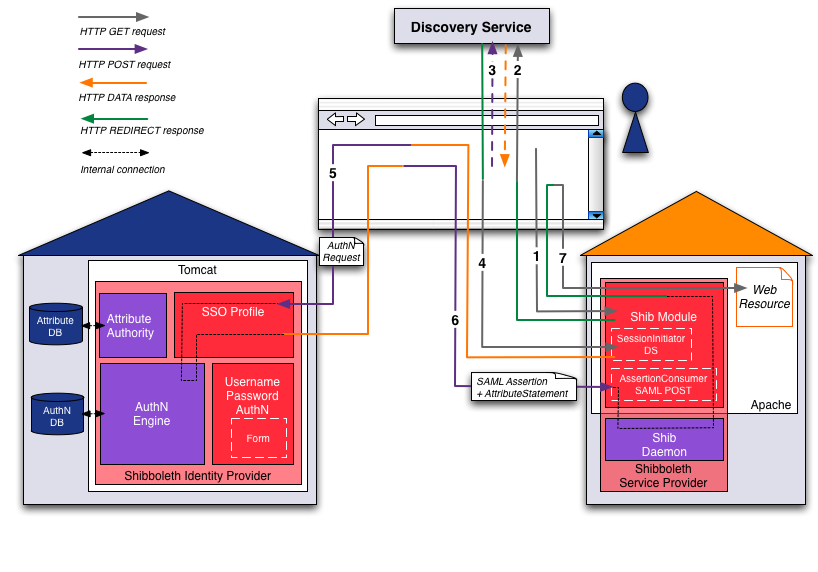
Identity Provider Session
Note: If the Discovery Service is setting a cookie containing the user's Identity Provider selection, the dashed steps are omitted and the user's web browser is redirected directly to the user's Identity Provider.
The Identity Provider checks the following:
- If a session already exists for the user
- If the session timeout is not exceeded (default: 30min)
- If the authentication method (e.g. PKI, UsernamePassword) timeout (inactivity) is not exceeded (UsernamePassword default: 30min)
- If the forceAuthn attribute is not set
If one of these points does not match, the Identity Provider will enforce an authentication for the user.
Both timeouts (session and authentication method) are based on inactivity,
they are updated during each authentication request.
If the session expires, all authentication method timeouts are cleared.
Expert Demo
| Take a look at the expert demo if you would like to see this login procedure in action. |