Interconnecting with Microsoft Environments
The world of Microsoft and edu-ID is constantly changing, so this page will be continuously updated.
|
Contents: |
 |
Introduction
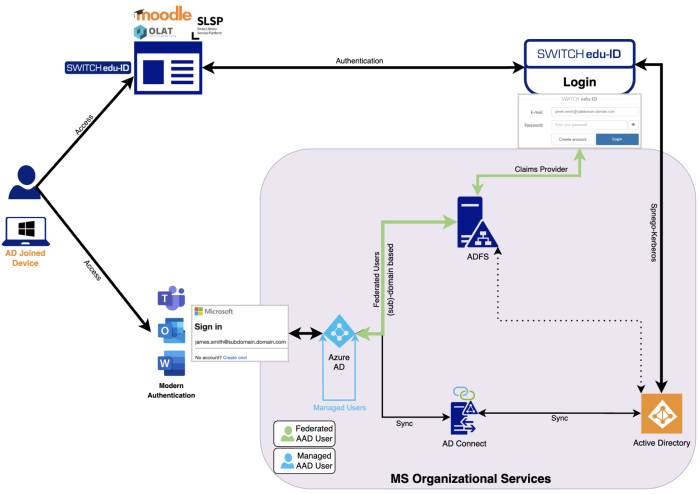
As organizations increasingly adopt Microsoft services, it's becoming more common to connect SWITCH edu-ID with existing Active Directory (AD) and Azure AD environments. This allows users to log in to cloud-based applications with a single SWITCH edu-ID credential, simplifying cross-organizational collaboration and student mobility.
Integrating an external identity provider with Azure AD or AD environments can be accomplished using various protocols, such as SAML 2.0, WS-Federation, or OpenID Connect. However, it's important to understand the differences between legacy and modern authentication methods within Microsoft to obtain the required integration overview.
Authentication methods
| Legacy Authentication | Modern Authentication |
|---|---|
|
Legacy authentication refers to the traditional authentication methods used in Microsoft environments that rely on usernames and passwords. These authentication methods were designed for on-premises environments and were not optimized for modern security requirements, such as multi-factor authentication, conditional access policies, and device-based authentication. This includes protocols such as POP, IMAP, SMTP, WS-Federation and WS-Trust. Microsoft is encouraging customers to adopt modern authentication methods that provide stronger security and better user experiences. |
Modern authentication in Microsoft environments refers to the use of OAuth 2.0, OpenID Connect, and SAML 2.0 protocols for authentication and authorization. These protocols support advanced security features such as multi-factor authentication, conditional access policies, and device-based authentication, and provide a more secure and seamless user experience compared to legacy authentication methods. SWITCH edu-ID supports SAML 2.0 and OpenID Connect. |
|
|
Best Practice: |
|
|
Requirement: |
Key terms of Microsoft:
We generally assume that the reader is familiar with Microsoft's key terms, so we will limit ourselves to a handful of terms that are essential.
- Active Directory
- (Azure) Active Directory (AAD/AD) is a directory service from Microsoft used to manage users, devices, and resources. It runs either in the Azure cloud or locally on an on-premise installation, with corresponding usage tradeoffs.
- AD Federation Services (ADFS) is a service that allows user federation for local on-premise ADs.
- Azure AD Connect is a tool that synchronizes user accounts, groups, and other objects between AD and AAD.
- Device Join
- Azure AD Join allows Windows devices to be managed by Azure AD what enables users to sign in to their devices using Azure AD credentials.
- Hybrid Azure AD Join enables users to sign in to their devices using their on-premises AD credentials.
- Azure AD Users
- Managed User is created and managed directly within Azure AD.
- Federated User is authenticated by an external Identity Provider (IdP) using federation protocols such as SAML.
- Guest User is an external user invited to access resources in a specific Azure AD tenant.
Interconnection Overview
|
|
For a long time, Microsoft neglected universities and NRENs when it came to proposing solutions for multilateral federations. As of June 2023, there is now official documentation on using Microsoft Azure AD with identity federations. Learn more |
Federating Azure AD with SWITCH edu-ID

| on-premise AD | Azure AD |
|
|
|
|
We advise organizations to contact the SWITCH edu-ID team (eduid-support@switch.ch) before starting the implementation. |
Advantages and Disadvantages Federating with SWITCH edu-ID
Federating Azure AD and AD with an external identity provider using SAML or OIDC allows for seamless and secure access to all resources using modern authentication, including M365 services.
|
Advantages |
Disadvantages |
|
|
Federating Azure AD and AD with SWITCH edu-ID
Federating SWITCH edu-ID with Azure AD means that a user from a given organization can use their university's Azure AD tenant credentials to log in to SWITCH edu-ID.