Authentication
A user, accessing a service must first authenticate at the IdP to prove his or her identity. The edu-ID service currently supports the following authentication methods
Single Sign-On
Switch edu-ID implements single sign-on to allow a user to log in once and subsequently access services without re-authentication during a session. SSO only works if the user keeps using the same device (browser).
The SSO session duration is set to 8 hours on the edu-ID IdP.
Users who authenticate with 2-step login can set an MFA session by checking "Don't ask again for 30 days" during authentication. The MFA session is set to 30 days by default, but can be changed by other factors (see below).
Multi-Factor Authentication
To increase authentication security Switch edu-ID supports strong or multi-factor authentication (MFA) with or without passwords:
- Password and 2-step login with TOTP or SMS
- Passkey with user identification
When a user configures Passkeys as authentication method, user verification is always enforced. Therefore, Passkey authentication always includes multi-factor authentication.
Authentication Policy
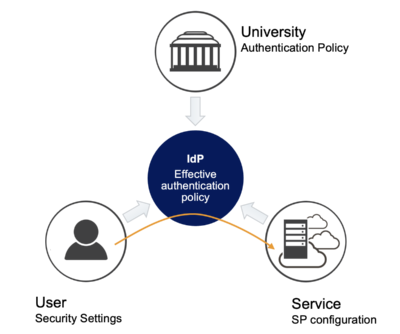 When a user accesses a service, an effective authentication policy is determined. This depends on the user's security settings, the service configuration and the university's organization policy.
When a user accesses a service, an effective authentication policy is determined. This depends on the user's security settings, the service configuration and the university's organization policy.
Users security settings
In the security settings of the account management (https://eduid.ch) a user can set the preferred authentication methods. The user can:
- choose between authentication with passwords or Passkeys
- define the preferred 2-step login method (TOTP or SMS)
- define whether 2-step login should always be requested ("always") or only if the service requires it ("on-demand")*
*) the on-demand option is deprecated.
Service configuration
A service has the following possibilities to define the authentification quality for its users:
- enforce MFA
- enforce re-authentication (disable or ignore SSO)
To support special use cases, Switch will develop a solution that allows users without MFA to access to services that enforce MFA. This feature is currently under development and will be released by end of 2024.
Organisation policy
Universities can set a default policy for all of their users, who have an organizational affiliation linked to their edu-ID account. It can define the following settings individually for each organizational member:
- enforce the usage of MFA
- define the set of allowed 2-step login factors (i.e. forbid the usage of SMS)
- define the MFA session duration
Determination of the effective authentication policy
When a user accesses a service his/her account settings, the service's configuration and the (possibly multiple) organization policies have to be combined into an effective authentication policy. This calculation is done in real time by the edu-ID IdP.
Generally, the various policies are combined additively towards stronger, more secure, more restrictive authentication.
Example 1
- Service does not require MFA
- Organisation enforces MFA with duration 30 days, and only TOTP
→ MFA is enforced with duration 30 days and only TOTP
Example 2
- Service does not require MFA
- Organisation A enforces MFA with 7 days duration, TOTP only
- Organisation B enforces MFA with 1 day duration, any type
- User does not set any custom MFA settings
→ MFA enforced with 1 day duration and TOTP only
Example 3
- Service requires MFA
- Organisation does not enforce MFA
→ MFA is enforced with duration 30 days
