SPNEGO-based Kerberos Authentication
What it is:
See this short video:
Introduction
Besides authentication with username and password, the edu-ID IdP supports SPNEGO-based Kerberos authentication for organisations operating a Microsoft Windows network with an Active Directory.
The SPNEGO-based Kerberos authentication (also known as Integrated Windows Authentication or Desktop Login in short for end users) enables users to seamlessly log in at the IdP with their Windows credentials, using Kerberos. This allows users to log into an application using their SWITCH edu-ID without having to enter username and password at the IdP.
This authentication method is supported for clients being members of the organisation's Windows domain. It's not supported for "road warrior" clients. the section Activation Conditions for Clients below explains how to select the clients that can use this authentication mechanism.
The SPNEGO-based Kerberos authentication of the SWITCH edu-ID is based on Kerberos Cross Realm Trust, as illustrated in the following picture:
Kerberos Cross Realm Trust:
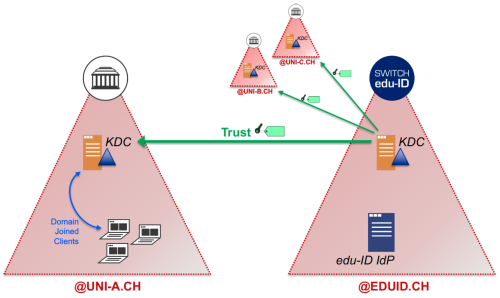
For detailed information, see the presentation SPNEGO-based Kerberos Authentication in SWITCH edu-ID.
Requirements
The SPNEGO-based Kerberos authentication can be supported by organisations fulfilling the following requirements:
- The organisation operates a Microsoft Windows network with Microsoft AD servers.
- The clients are joined to the Windows domain.
- The organisation allows the edu-ID Kerberos realm to trust the organisation's Windows Kerberos realm.
- The organisation populates / synchronizes the Kerberos Principal Names of all their users into the affiliations of the respective SWITCH edu-ID accounts (into the attribute extKerberosPrincipalName)
Supported server and client systems
| Windows Server | Windows Server 2012 R2 Windows Server 2016 Windows Server 2019 |
| Windows Desktop | All windows desktop versions supported by Microsoft |
| Others | macOS Linux |
Setup instructions for the organisation
The organisation needs to configure its environment as described in the following sections in order to support the SPNEGO-based Kerberos authentication.
Important settings for the SWITCH edu-ID Kerberos realm:
| Kerberos realm | EDUID.CH |
| KDC servers | kdc1.eduid.chkdc2.eduid.ch |
| Service DNS names | login.eduid.ch*.login.eduid.ch |
Some of the examples below use the example domain uni-demo.ch and the corresonding Kerberos realm UNI-DEMO.CH. You need to adapt the examples to match your environment.
Prerequisites
Negotiate a password for Kerberos Cross Realm trust with SWITCH
To configure Kerberos Cross Realm trust, both realms, the organisation's realm and the SWITCH edu-ID realm need to share a common principal krbtgt/EDUID.CH@UNI-DEMO.CH.
Since SWITCH needs to add the same principal to the @EDUID.CH realm, the organisation and SWITCH need to negotiate a shared password. Please contact the SWITCH edu-ID team to get this password and inform us about your REALM name. It will be used in the section Configure trust for the Kerberos realm EDUID.CH below.
Provide the attribute extKerberosPrincipalName in affiliations
During the login via SPNEGO, the edu-ID IdP needs to find the edu-ID account corresponding to the identifier presented in the Kerberos ticket. Ths identifier is usually composed from the sAMAccountName attribute and the Kerberos realm, e.g. ataylor@UNI-DEMO.CH.
The organisation must provide this value in the affiliations' attribute extKerberosPrincipalName via the chosen synchronization mechanism. See Managing affiliations for details.
Configuration required on the Windows AD server
Configure Kerberos Cross Realm Trust from the SWITCH edu-ID realm to the organisation's realm.
Overview:
- Configure trust for the Kerberos realm EDUID.CH
- Add a GPO to configure the Kerberos client settings for the realm EDUID.CH
All these steps are executed on the Windows AD server. Log in to the server as user with domain administration privileges.
1. Configure trust for the Kerberos realm EDUID.CH
- Open the Server Manager
- Open Tools / Active Directory Domains and Trusts
- Select your domain and open Properties.
- Change to the Trusts tab.
- Click New Trust...
- Follow the wizard and choose the following settings:
- Trust Name: Name: EDUID.CH
- Trust Type: Select Realm trust
- Transitivity of Trust: Select Nontransitive
- Direction of Trust: Select One-way: incoming
- Trust Password: Enter the password negotiated with SWITCH (see Prerequisites above)
- Select the new trust, open Properties and make sure that the checkbox The other domain supports Kerberos AES Encryption is checked.
Note: Alternatively, you can use the command netdom trust EDUID.CH /Domain:UNI-DEMO.CH /add /realm /passwordt:... in a terminal, but you need to pass the password as argument to the command. If you know of a better alternative using PowerShell, please let us know.
Validate the settings:
Run the following command in Power Shell (example for the domain unidemo.ch):
netdom query /Domain:UNI-DEMO.CH trust
Make sure that you can see the configured domain trust.
2. Add a GPO to configure the Kerberos client settings for the realm EDUID.CH
- Open the Server Manager
- Open Group Policy Management
- Expand Forest: <your domain> / Domains / <your domain> / Group Policy Objects
(e.g. Forest: uni-demo.ch / Domains / uni-demo.ch / Group Policy Objects) - Create a new GPO named "Kerberos Realm EDUID.CH"
- Select the new GPO and edit it (choose Edit...)
- Expand Computer Configuration > Policies > Administrative Templates > System > Kerberos
- Configure and enable the following settings in Kerberos:
- Define Interoperable Kerberos V5 realm settings
- Set to Enabled
- Select Show... and enter:
- Value name: EDUID.CH
- Value: <f>0x2</f> <k>kdc1.eduid.ch; kdc2.eduid.ch</k>
- Define host name-to-Kerberos realm mappings
- Set to Enabled
- Select Show... and enter:
- Value name: EDUID.CH
- Value: login.eduid.ch; .login.eduid.ch
- Define Interoperable Kerberos V5 realm settings
Note: This configuration may also be applied using appropriate commands in PowerShell.
Validate the settings:
Run the following commands in Power Shell:
get-gpregistryvalue -name "Kerberos Realm EDUID.CH" -key "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\Kerberos\MitRealms" get-gpregistryvalue -name "Kerberos Realm EDUID.CH" -key "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\Kerberos\domain_realm"
Make sure that you can see the settings configured above.
Configuration required on the Windows clients
Apply the Kerberos settings configured via GPO on the server and configure the web browsers to support the SPNEGO/Kerberos login option.
Overview:
- Apply the Kerberos Group Policy configured on the server
- Configure the web browsers to support the SPNEGO/Kerberos login option
1. Apply the Kerberos Group Policy configured on the server
Restart the Windows clients or run gpupdate /force to update and apply the GPO.
Validate the settings:
Run the following commands on the client in Power Shell as a user with Administration privileges:
gpresult /R /SCOPE COMPUTER
In the section Applied Group Policy Objects, you should find the GPO where you specified the Kerberos settings (e.g. Kerberos Realm EDUID.CH):
Applied Group Policy Objects
-----------------------------
Default Domain Policy
Kerberos Realm EDUID.CH
Local Group Policy
The following command allows to see the two settings:
gpresult /V /SCOPE COMPUTER
You should find the two settings specified above:
Administrative Templates
------------------------
...
GPO: Kerberos Realm EDUID.CH
Folder Id: Software\Microsoft\Windows\CurrentVersion\Policies\System\Kerberos\domain_realm\EDUID.CH
Value: ...
State: Enabled
GPO: Kerberos Realm EDUID.CH
Folder Id: Software\Microsoft\Windows\CurrentVersion\Policies\System\Kerberos\MitRealms\EDUID.CH
Value: ...
State: Enabled
...
(Alterantively, you can use the Resultant Set of Policy tool "rsop.msc" to validate the settings.)
2. Configure the web browsers to support the SPNEGO/Kerberos login option
Please refer to the instructions at Browser configuration for SPNEGO-based Kerberos authentication provided by the Shibboleth IdP documentation.
The following URLs must be configured as trusted:
-
https://login.eduid.ch
-
https://<org>.login.eduid.ch
(<org> denotes the domain label assigned to your organisation; ask the edu-ID team in case you haven't received this information.)
Note: Organisations may configure these settings using their central configuration management system.
Troubleshooting
- Check if the Kerberos Group Policy has been applied on the client
- Log in to the client with a user with administrator privileges
- Run the Resultant Set of Policy tool "rsop.msc"
- Check if the two policies exist:
- Computer Configuration / Adminsitrative Templates / System / Kerberos / Define host name-to-Kerberos realm mappings
- Computer Configuration / Adminsitrative Templates / System / Kerberos / Define interoperable Kerberos V5 realm settings
Configuration required on other operating systems
macOS
Prerequisite:
- The user must have a working Kerberos configuration for the organisation's own Kerberos realm.
Users need to add the following configuration to their existing /etc/krb5.conf file:
- Section [realms]:
EDUID.CH = {
kdc = tcp/kdc1.eduid.ch
kdc = tcp/kdc2.eduid.ch
} - Section [domain_realm]:
.eduid.ch = EDUID.CH
Linux
Prerequisite:
- The user must have a working Kerberos configuration for the organisation's own Kerberos realm.
Users need to add the following configuration to their existing /etc/krb5.conf file:
- Section [realms]:
EDUID.CH = {
kdc = tcp/kdc1.eduid.ch
kdc = tcp/kdc2.eduid.ch
} - Section [domain_realm]:
.eduid.ch = EDUID.CH
Testing
Windows
Can a ticket for the edu-ID IdP service be requested?
Try to get a Kerberos ticket in the command line terminal:
- Open the command line terminal (Windows-R, type "cmd")
- Run "klist" to show the current Kerberos tickets. You should see a ticket for your own user.
C:\Users\alex.taylor>klist
...
#0> Client: alex.taylor @ UNI-DEMO.CH
Server: krbtgt/EDUID.CH @ UNI-DEMO.CH
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40a50000 -> forwardable renewable pre_authent ok_as_delegate name_canonicalize
Start Time: 9/4/2023 14:58:19 (local)
End Time: 9/5/2023 0:58:19 (local)
Renew Time: 9/11/2023 14:57:39 (local)
Session Key Type: AES-256-CTS-HMAC-SHA1-96
Cache Flags: 0
Kdc Called: dc1.uni-demo.ch
#1> ... - Try to get a ticket for HTTP/login.eduid.ch@EDUID.CH.
You should get a new ticket for HTTP/login.eduid.ch@EDUID.CH.
C:\Users\alex.taylor>klist get HTTP/login.eduid.ch@EDUID.CH
...
#2> Client: alex.taylor @ UNI-DEMO.CH
Server: HTTP/login.eduid.ch @ EDUID.CH
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40290000 -> forwardable pre_authent name_canonicalize 0x80000
Start Time: 9/4/2023 15:09:52 (local)
End Time: 9/5/2023 1:09:52 (local)
Renew Time: 0
Session Key Type: AES-256-CTS-HMAC-SHA1-96
Cache Flags: 0
Kdc Called: kdc1.eduid.ch
...
Activation Conditions for Clients
The SPNEGO mechanism used for the Integrated Windows Authentication has some shortcoming that doesn't allow the IdP to check whether a client supports login via Kerberos or not. For users of Internet Explorer or Edge without specific configuration, this can lead to a situation where the Internet Explorer/Edge locally asks for username and password while falling back to the NTLM mechanism.
To avoid this confusing situation, the IdP allows to limit offering SPNEGO to a certain set of clients by configuring appropriate activation conditions. These conditions can be based on the client's IP address, the client's user agent identifier string, or other information available during the HTTP communication.
The organisation needs to define a suitable set of conditions that specify for which clients the IdP should enable Integrated Windows Authentication.
SWITCH will implement the conditions specified by the organisation on the edu-ID IdP.
Examples of activation conditions:
- Based on the client's IP address: The clients are in a network with a dedicated IP range. All clients in this IP range are assumed to support Kerberos. The edu-ID IdP will offer the SPNEGO/Kerberos login to all clients in this IP range.
- Based on the web browsers user agent identifier string: Organisations can configure the web browsers' user agent string to contain a certain keyword that allows the edu-ID IdP to recognise the browser to support Kerberos. For such browsers, the edu-ID IdP will offer the SPNEGO/Kerberos login.