Under each of your OpenStack Projects, you will find a Security Group called default. Initially it will contain four rules that look like this:
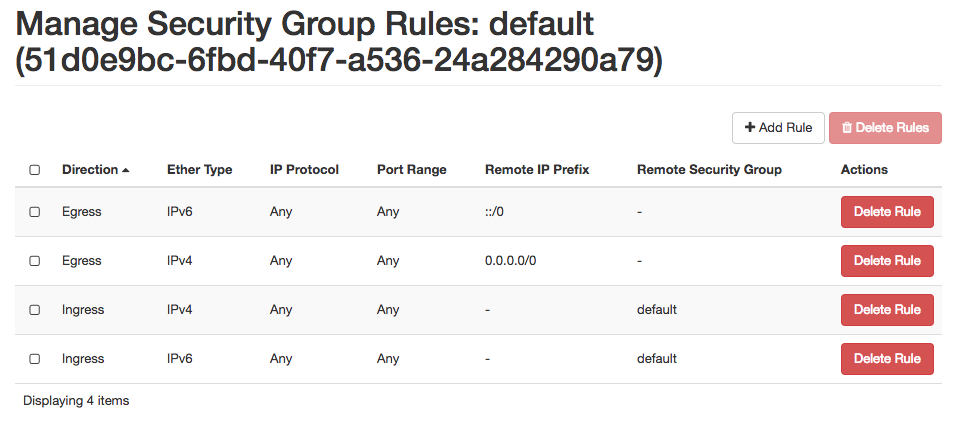
What do these rules mean? Note that the rules come in pairs, one for IPv4 and one for IPv6—you generally want both.
The first pair are "egress" rules. They allow traffic from your instance to anywhere on the Internet. This makes it possible for your instance to initiate connections to the outside. This is necessary for things such as:
- Accessing operation system package distributions for regular software updates
- DNS requests for converting hostnames to IP addresses (for example to find the servers mentioned above)
- Querying Network Time Protocol (NTP) servers to discipline the system clock
- Accessing the OpenStack Metadata Service during system boot.
The second pair are "ingress" rules that allow all incoming traffic from other members of the same security group. Thus, when you create several instances sharing this Security Group, they will have unlimited connectivity between each other—you won't need any specific rules to allow those internal communications.
Note that no other traffic is allowed by default. In particular, external hosts will not be able to connect to your instances unless you explicitly allow that by adding your own Security Groups/rules.
You may be tempted to remove these four default rules in order to improve security, but there are important caveats:
If you delete the egress rules altogether, your instances will take a long time to start up, because they won't be able to access the Metadata Service. They will also miss the information from that service. In particular, they won't be able to provision the trusted SSH public key for the default account. So unless you have configured SSH authorization in some other way, you won't be able to log in.
We mentioned a few other uses of the egress rules: Our standard images are configured to periodically check for and download software updates, which is considered a best practice for security reasons. They will also synchronize their system clocks using remote NTP servers. Without the egress rules that won't work.
The ingress-from-same-security-group rules are less critical. If you remove them, you will simply have to explicitly allow traffic from your other instances, in the same way as you have to allow traffic from external hosts.